Breaking News

Popular News


Learn best practices for ChatGPT API security, data encryption, access controls, monitoring, and compliance with security standards to protect your data.In today’s interconnected digital world, the need for robust security measures to protect sensitive data cannot be overstated. As organizations increasingly integrate AI-driven chatbot solutions like OpenAI’s ChatGPT API into their operations, ensuring the security of the data transmitted through these systems becomes paramount. This blog post will explore the essential best practices for securing ChatGPT API data, covering topics such as understanding the specific security considerations of the API, assessing data protection needs, implementing encryption measures, managing access controls, monitoring and auditing data access, and ensuring compliance with security standards. By delving into these areas, businesses can gain a comprehensive understanding of the measures necessary to safeguard their data effectively. Whether you’re a developer, IT professional, or business owner looking to strengthen your cybersecurity posture, this guide aims to provide actionable insights for fortifying your ChatGPT API security framework.
Contents

When it comes to understanding ChatGPT API security, it is crucial to consider the best practices for data protection. As the use of AI and machine learning continues to grow, ensuring the security of API connections becomes increasingly important. ChatGPT, with its advanced language model, is no exception.
One of the key aspects of ChatGPT API security is assessing data protection needs. This involves understanding the types of data that will be transmitted via the API, as well as the potential vulnerabilities and threats that could impact the security of that data. Identifying and assessing these needs is a crucial first step in implementing effective security measures.
Another important consideration for ChatGPT API security is implementing data encryption measures. Encryption helps to protect sensitive data from unauthorized access and ensures that only authorized parties can decipher and make use of the information. By encrypting data transmitted through the API, organizations can significantly enhance their overall security posture.
Lastly, managing access controls is a critical aspect of ChatGPT API security. By carefully defining who can access the API and what actions they are permitted to perform, organizations can reduce the risk of unauthorized data access and misuse. Implementing strong access controls is essential for maintaining the integrity and security of the API.
Assessing Data Protection Needs
When it comes to safeguarding your organization’s sensitive data, it’s essential to start by assessing your data protection needs. This means taking a comprehensive look at the types of data your organization collects, processes, and stores, as well as the potential risks and consequences of a data breach. One key consideration in this assessment is the classification of your data – determining which information is most critical and in need of the highest level of protection.
Another important aspect of assessing data protection needs is evaluating the legal and regulatory requirements that apply to your organization. Depending on your industry and the geographic locations in which you operate, there may be specific laws and standards governing data protection that must be adhered to. This can include requirements related to data retention, privacy, and security practices.
Additionally, it’s crucial to consider the potential threats to your organization’s data, including both internal and external risks. This may involve conducting a risk assessment to identify vulnerabilities and potential attack vectors, as well as assessing the impact of a data breach on your organization’s operations and reputation.
Ultimately, by thoroughly assessing your data protection needs, you can develop a clear understanding of the specific measures and safeguards that are necessary to protect your organization’s sensitive information from unauthorized access, disclosure, and misuse.
One of the most important aspects of data security is implementing effective data encryption measures. Encrypting sensitive data ensures that even if unauthorized users gain access to the data, they will not be able to read or make use of it. This is crucial for protecting personal and sensitive information from cyber threats.
When it comes to implementing data encryption measures, it’s important to use strong encryption algorithms such as AES (Advanced Encryption Standard) to encode the data. Additionally, companies should make use of encryption key management systems to securely store and oversee encryption keys to ensure that only authorized users have access to them.
Furthermore, it’s essential to use end-to-end encryption to secure data both in transit and at rest. This means that the data is encrypted from the moment it is created, throughout its storage and transmission, all the way to its destination. By implementing end-to-end encryption, organizations can ensure that their data remains protected at every stage.
Ultimately, implementing robust data encryption measures is critical for safeguarding sensitive information and ensuring data security compliance with industry standards and regulations.
Managing access controls is an essential aspect of maintaining data security within an organization. By implementing access controls, organizations can effectively manage who has access to sensitive data, preventing unauthorized individuals from obtaining confidential information.
One of the key best practices for managing access controls is to regularly assess and update user permissions. It is important to review user access levels and modify them as necessary to ensure that individuals only have access to the specific data and systems required for their job roles.
Additionally, organizations should consider implementing multi-factor authentication (MFA) to add an extra layer of security to access controls. MFA requires users to provide two or more forms of verification before gaining access to sensitive data, such as a password and a unique code sent to their mobile device.
| User | Access Level |
|---|---|
| John Doe | Administrator |
| Jane Smith | Read-Only |
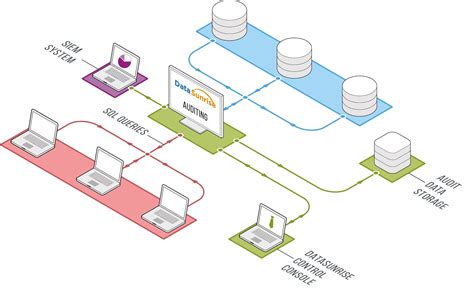
Monitoring and Auditing Data Access
Monitoring and Auditing Data Access
Monitoring and auditing data access are critical components of ensuring the security of an organization’s sensitive information. By implementing a robust system for monitoring and auditing data access, businesses can track who is accessing their data, when it is being accessed, and what actions are being performed on it. This can help identify and respond to any unauthorized or suspicious activity that could pose a threat to the integrity and confidentiality of the data.
One effective way to monitor data access is through the use of audit logs. Audit logs provide a record of all access and usage of data, including logins, file access, and changes made to the data. These logs should be regularly reviewed and analyzed to identify any anomalies or potential security breaches. In addition, implementing real-time monitoring tools can provide instant alerts for any unauthorized access attempts, allowing for swift action to be taken to mitigate any potential risks.
Furthermore, it is crucial to establish clear access control policies and procedures to govern who has access to sensitive data and under what circumstances. This can help limit the potential for unauthorized access and ensure that only authorized individuals are able to view or modify the data. Regular access reviews should also be conducted to verify that access privileges are assigned appropriately and that any unnecessary access is promptly revoked.
| Data Access Monitoring Best Practices | Benefits |
|---|---|
| Implementing audit logs | Real-time alerts for unauthorized access attempts |
| Establishing clear access control policies | Limits potential for unauthorized access |
| Conducting regular access reviews | Verify and revoke unnecessary access |
By prioritizing monitoring and auditing data access, businesses can take proactive steps to protect their sensitive information and mitigate the risks associated with unauthorized access. These best practices can contribute to a comprehensive security strategy that safeguards data integrity, confidentiality, and availability against potential threats and vulnerabilities.

When it comes to security standards, compliance is a critical aspect of protecting data and maintaining trust with customers. Organizations must adhere to industry regulations and best practices to avoid the risks of data breaches and cyber attacks. By ensuring compliance with security standards, businesses can demonstrate their commitment to safeguarding sensitive information.
One way to ensure compliance with security standards is to conduct regular audits and assessments of security measures. This involves reviewing security policies, procedures, and controls to identify any gaps or vulnerabilities that may exist. By regularly monitoring and evaluating security practices, organizations can take proactive steps to address any non-compliance issues before they escalate into major security threats.
Additionally, implementing access controls is essential for maintaining compliance with security standards. By defining and managing access rights to data and systems, organizations can prevent unauthorized access and minimize the risk of data exposure. Access control measures such as role-based access, multi-factor authentication, and encryption can help enforce security protocols and ensure compliance with industry regulations.
Overall, ensuring compliance with security standards is crucial for protecting sensitive data and upholding the trust of customers. By implementing robust security measures, conducting regular audits, and managing access controls, organizations can demonstrate their commitment to maintaining the highest levels of data protection and compliance with industry standards.

What is ChatGPT API?
The OpenAI ChatGPT API is a text generation model that can be integrated into applications to generate human-like responses to text input.
Why is API security important for ChatGPT?
API security is important for ChatGPT to protect the sensitive data and information that may be exchanged through the API, ensuring privacy and preventing unauthorized access.
What are the best practices for securing ChatGPT API data?
Best practices for securing ChatGPT API data include using encryption for data transmission, implementing authentication and access controls, regularly updating and patching the API, and monitoring for any unauthorized access or activities.
How does encryption help in securing ChatGPT API data?
Encryption helps in securing ChatGPT API data by encoding the information in a way that can only be deciphered by authorized parties, preventing unauthorized access to sensitive data.
What authentication methods can be used to secure ChatGPT API?
Authentication methods such as API keys, OAuth, and JWT tokens can be used to secure ChatGPT API, ensuring that only authorized users and applications can access the API.
Why is regular updating and patching important for ChatGPT API security?
Regular updating and patching are important for ChatGPT API security to address any vulnerabilities or security flaws that may be discovered, ensuring that the API remains secure against potential threats.
How can monitoring help in maintaining the security of ChatGPT API?
Monitoring can help in maintaining the security of ChatGPT API by tracking and analyzing the API’s usage, detecting any suspicious activities, and responding to potential security incidents in a timely manner.