Breaking News

Popular News


Stay ahead of cyber threats with insights on evolution, impact of digitalization, common attack methods, effective strategies, AI’s role, and future trends in cybersecurity. Protect your digital assets.In the digital age, the rise of cybersecurity threats has become a major concern for individuals and organizations alike. As our world becomes increasingly interconnected, the need for robust cybersecurity measures has never been more critical. From understanding the various types of cybersecurity threats to the evolution of cybersecurity measures, it’s essential to stay informed about the impact of digitalization on cybersecurity. Common cybersecurity attack methods are constantly evolving, making it crucial to implement effective cybersecurity strategies to safeguard against potential breaches and attacks. Additionally, the role of artificial intelligence in cybersecurity is becoming increasingly important, offering new ways to combat threats in real-time. As we look towards the future, it’s essential to stay ahead of emerging trends in cybersecurity threats to protect ourselves and our digital assets. Join us as we explore the ever-changing landscape of cybersecurity and discuss how to stay one step ahead in an increasingly digital world.
Contents

In the fast-paced world of technology, cybersecurity threats continue to evolve and pose significant challenges to individuals, businesses, and governments. It is crucial to have a clear understanding of these threats in order to effectively protect sensitive information and systems from potential breaches.
Cybersecurity threats can come in various forms, including malware, phishing attacks, ransomware, and insider threats. Malware, short for malicious software, is designed to damage or gain unauthorized access to a computer system. Phishing attacks involve deceiving individuals into providing sensitive information, while ransomware locks users out of their systems until a ransom is paid. Insider threats are posed by individuals within an organization who misuse their access to sensitive data for personal gain or malicious intent.
| Threat Type | Description |
|---|---|
| Malware | Designed to damage or gain unauthorized access to a computer system |
| Phishing attacks | Deceiving individuals into providing sensitive information |
| Ransomware | Locks users out of their systems until a ransom is paid |
| Insider threats | Misuse of access to sensitive data by individuals within an organization |
Understanding the nuances of these cybersecurity threats is essential for developing and implementing effective strategies to mitigate the risks they pose. As technology continues to advance, it is crucial for individuals and organizations to stay informed and proactive in addressing evolving cybersecurity threats.

In the ever-changing digital landscape, the evolution of cybersecurity measures has become increasingly crucial. As cyber threats continue to grow in complexity and volume, organizations are constantly adapting their security protocols to keep up with the pace of technological advancements. From the early days of simple firewalls and antivirus software, the evolution of cybersecurity measures has seen the emergence of more sophisticated tools such as threat intelligence platforms and advanced encryption algorithms.
Internet security protocols that were once deemed sufficient are no longer able to provide effective protection against the myriad of cybersecurity threats faced by organizations today. As a result, the evolution of cybersecurity measures has shifted towards a more proactive approach, with an emphasis on threat detection and incident response capabilities.
Collaboration and information sharing among cybersecurity professionals have also played a significant role in the evolution of cybersecurity measures. The cybersecurity community has recognized the value of collective intelligence in combating cyber threats, leading to the development of collaborative defense strategies and information sharing platforms.
Overall, the continuous evolution of cybersecurity measures is a testament to the ongoing battle against cyber threats. As technology continues to advance, so too must the security protocols implemented by organizations to protect their digital assets.
Impact of Digitalization on Cybersecurity
Impact of Digitalization on Cybersecurity
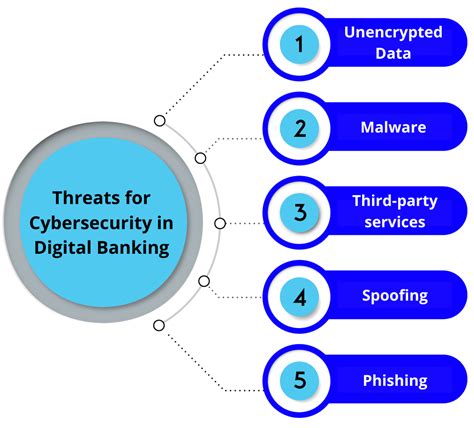
The digital age has brought numerous benefits and conveniences to our lives. However, it has also introduced new cybersecurity challenges that organizations and individuals must address. As more and more aspects of our lives become digitalized, such as banking, communication, and entertainment, the amount of sensitive data being transferred and stored online has increased exponentially.
This has created a prime target for cyber attackers who seek to exploit vulnerabilities in digital systems for their own gain. With the rapid digital transformation of businesses and society as a whole, the attack surface for cyber threats has expanded, requiring a more proactive and comprehensive cybersecurity approach.
Organizations are now faced with the challenge of securing a myriad of digital devices and systems, from end-point devices to cloud infrastructure. The shift towards remote work and the Internet of Things (IoT) has further increased the complexity of cybersecurity management, as each new digital connection presents a potential entry point for malicious actors.
Adapting to the impact of digitalization on cybersecurity requires a multi-faceted approach that includes advanced threat detection, encryption technologies, user awareness training, and regular security audits. As we continue to embrace digitalization, it is imperative that we also prioritize the protection of our digital assets against evolving cyber threats.
Common Cybersecurity Attack Methods
Common Cybersecurity Attack Methods
In today’s digital age, the threat of cybersecurity attacks looms large over individuals and organizations alike. Cybercriminals are constantly finding new and innovative ways to breach security measures and access sensitive information. It is essential to understand the common methods employed by these attackers in order to effectively safeguard against them.
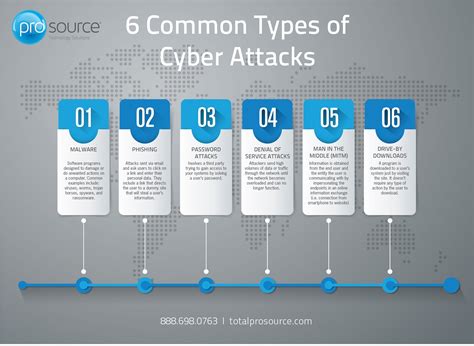
One of the most prevalent cybersecurity attack methods is phishing, where attackers use deceptive emails or websites to trick individuals into providing confidential information such as passwords or financial details. This method often targets unsuspecting users and can have devastating consequences if successful.
Malware is another common attack method, involving the use of malicious software to infiltrate and damage computer systems. This can include viruses, ransomware, and spyware, all of which can compromise sensitive data and disrupt normal operations.
Denial-of-Service (DoS) attacks are also frequently used by cybercriminals to overwhelm a network or website with a flood of traffic, causing it to become inaccessible to legitimate users. This can have serious implications for businesses and individuals who rely on online services for their daily activities.
| Common Cybersecurity Attack Methods | Description |
|---|---|
| Phishing | Deceptive emails or websites used to obtain sensitive information |
| Malware | Malicious software designed to infiltrate and damage computer systems |
| Denial-of-Service (DoS) attacks | Overwhelming a network or website with a flood of traffic, making it inaccessible |
It is crucial for individuals and organizations to be aware of these common cybersecurity attack methods and take proactive measures to protect against them. This includes implementing strong security protocols, educating users about potential threats, and regularly updating and patching systems to prevent vulnerabilities from being exploited.
When it comes to protecting your digital assets, the implementation of effective cybersecurity strategies is paramount. With the increasing number of cyber threats in the digital age, organizations and individuals must be proactive in safeguarding their networks and data. One of the key steps in implementing effective cybersecurity strategies is to conduct a thorough risk assessment to identify potential vulnerabilities and areas of weakness.
Once the risks have been identified, it is important to prioritize them and develop a comprehensive plan for mitigating these risks. This may involve implementing strong encryption methods, multi-factor authentication, and regular security updates. Additionally, organizations should establish clear policies and procedures for data access and usage, as well as provide ongoing training for employees to ensure they understand and adhere to cybersecurity best practices.
Another critical aspect of effective cybersecurity strategies is to regularly monitor and analyze network activity for any signs of unauthorized access or unusual behavior. This can be achieved through the use of advanced security tools and technologies, such as intrusion detection systems and security information and event management (SIEM) software. By proactively monitoring network activity, organizations can quickly detect and respond to potential security threats before they escalate into major incidents.
Finally, it is essential for organizations to have a robust incident response plan in place to effectively manage and contain any cybersecurity breaches. This may involve establishing a designated response team, conducting regular drills and simulations, and collaborating with external cybersecurity experts and law enforcement agencies when necessary. By having a well-defined incident response plan, organizations can minimize the impact of cyber attacks and rapidly restore the security and integrity of their networks and data.

Artificial intelligence (AI) has revolutionized the field of cybersecurity by providing advanced tools and techniques to combat evolving cyber threats. With the increasing complexity of cyber attacks, traditional security measures are no longer sufficient to protect sensitive data and networks. This is where AI comes into play, offering proactive defense mechanisms to effectively detect and respond to potential security breaches.
One of the primary roles of AI in cybersecurity is its ability to analyze vast amounts of data in real-time, identifying patterns and anomalies that may indicate malicious activities. This proactive approach enables organizations to stay ahead of threats and preemptively mitigate risks before they escalate into full-blown cyber attacks.
Moreover, AI-powered cybersecurity systems can autonomously adapt and learn from new threats, constantly evolving to stay one step ahead of cybercriminals. By utilizing machine learning algorithms, AI can identify and prioritize security vulnerabilities, enabling security teams to focus on critical areas that require immediate attention.
Additionally, AI plays a crucial role in enhancing incident response capabilities, enabling organizations to efficiently investigate security alerts and rapidly contain potential breaches. Through automated threat hunting and predictive analysis, AI equips security professionals with the necessary insights to make informed decisions and take proactive measures to safeguard their digital assets.
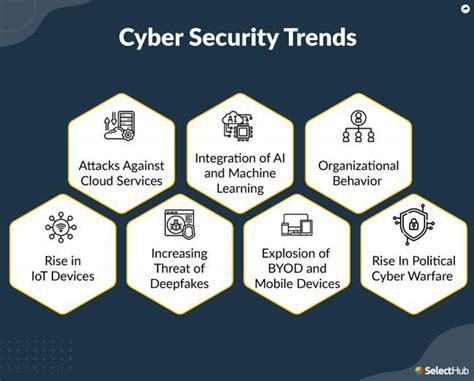
The future of cybersecurity threats is a topic that is constantly evolving as technology advances. With the rise of artificial intelligence and the increasing interconnectivity of devices, it is important to stay vigilant against emerging threats. One trend that is likely to continue is the use of AI-powered attacks, where cybercriminals leverage machine learning algorithms to breach security systems. These attacks are becoming more sophisticated and difficult to detect, making it challenging for traditional cybersecurity measures to keep up.
Another future trend in cybersecurity threats is the targeting of Internet of Things (IoT) devices. As more devices become connected to the internet, such as smart home appliances and wearable technology, they become potential targets for cyber-attacks. Weak security measures in these devices make them vulnerable to exploitation, posing a significant threat to personal privacy and security.
Additionally, the shift towards remote work and cloud-based systems has opened up new avenues for cybercriminals to exploit. The COVID-19 pandemic has accelerated the adoption of remote work, leading to an increase in cyber threats targeting home networks and online collaboration tools. As more organizations rely on cloud services to store and access data, there is a greater risk of data breaches and unauthorized access.
In response to these emerging trends, cybersecurity professionals are developing new strategies and technologies to mitigate the evolving threats. From implementing advanced threat detection systems to improving employee training on cybersecurity best practices, the future of cybersecurity will require a proactive and multi-layered approach to defense.

What are the common types of cybersecurity threats?
Common types of cybersecurity threats include malware, phishing attacks, ransomware, and DDoS attacks.
How can individuals protect themselves from cybersecurity threats?
Individuals can protect themselves by using strong, unique passwords, keeping their software updated, using antivirus software, and being cautious of suspicious emails and links.
What are the potential consequences of cybersecurity attacks?
The potential consequences of cybersecurity attacks include financial loss, damage to reputation, loss of sensitive information, and disruption of business operations.
How are businesses addressing cybersecurity threats?
Businesses are addressing cybersecurity threats by implementing security measures such as firewalls, encryption, employee training, and incident response plans.
What role does technology play in cybersecurity threats?
Technology both enables cybersecurity threats and provides solutions for defending against them. Advances in technology make it easier for hackers to exploit vulnerabilities, but also provide tools for detecting and preventing attacks.
What are the current trends in cybersecurity threats?
Current trends in cybersecurity threats include an increase in ransomware attacks, the targeting of remote workers, and the use of AI and machine learning by cybercriminals.
How can society as a whole mitigate cybersecurity threats?
Society as a whole can mitigate cybersecurity threats by promoting cybersecurity education and awareness, investing in research and development of security technologies, and collaborating with law enforcement agencies and cybersecurity professionals.